AI Powered Cybersecurity: The next generation of Cybersecurity
Fujitsu / March 31, 2025
AI is reshaping industries, and cybersecurity is one of its most critical applications. As cyber threats grow in complexity and scale, traditional security measures struggle to keep pace. AI-driven security solutions introduce a new paradigm, leveraging machine learning (ML), automation, and predictive analytics to enhance defense mechanisms. This article explores the intersection of AI and IT security, emphasizing its role in delivering the next generation of cybersecurity.
Contents
- The evolving threat landscape
- How AI transforms cybersecurity
- The business case for AI-driven security
- Challenges and considerations in AI security
- Future trends in AI powered security
- Fujitsu’s AI-enhanced security solutions
- Fujitsu’s multi-AI agent security technology
- Multi-AI agent collaboration
- Generative AI security enhancement
- AI-driven data and security technologies
- Fujitsu intelligence-led cybersecurity services
- Conclusion
The evolving threat landscape
The digital age has brought unprecedented connectivity, but it has also introduced sophisticated cyber threats. Ransomware, phishing attacks, insider threats, and state-sponsored cyber warfare have become routine. Traditional security models firewalls, signature based detection or Genotyping , and rule based monitoring are proving inadequate against adversaries who leverage automation and AI to infiltrate networks.
Organizations face a growing challenge: securing increasingly complex infrastructures while managing vast amounts of security data. AI provides the agility and intelligence required to combat these evolving threats in real time.
How AI transforms cybersecurity
The ability of AI to rapidly analyze large datasets, identify anomalies, and automate responses is transforming cybersecurity, including:
1. Threat detection and anomaly identification
Traditional security systems rely on predefined rules to detect threats. AI-driven security systems use ML algorithms to recognize deviations from normal patterns. By continuously learning from network behavior, AI can identify subtle anomalies that might indicate malicious activities, such as unauthorized access attempts, insider threats, or zero-day exploits.
2. Automated incident response and mitigation
Speed is crucial in cybersecurity. AI-powered systems can autonomously detect and respond to threats in real time, reducing response times from hours to milliseconds. Automated security orchestration enables AI to isolate infected endpoints, terminate malicious processes, and patch vulnerabilities without human intervention, significantly reducing potential damage.
3. Behavioral analysis and user authentication
AI-driven User and Entity Behavior Analytics (UEBA) enhances identity and access management. By analyzing login patterns, system usage, and user behavior, AI can detect unauthorized access attempts and insider threats. If an employee’s login credentials are compromised, AI can flag unusual behavior such as logins from different locations in short intervals and enforce additional security measures.
See: The future of cybersecurity - An introduction to ambient authentication https://corporate-blog.global.fujitsu.com/fgb/2024-09-12/01/
4. Predictive threat intelligence
AI enhances cybersecurity by predicting and preventing attacks before they happen. By analyzing past attacks, dark web activity, and security logs, AI can identify potential future threats and help organizations take proactive measures. AI-powered threat intelligence platforms enable security teams to stay ahead of attackers rather than merely reacting to incidents.
5. Enhanced endpoint and network security
AI strengthens endpoint security by recognizing malware, detecting ransomware patterns, and preventing unauthorized data exfiltration. Network security is similarly improved by AI-driven intrusion detection systems (IDS) and intrusion prevention systems (IPS), which continuously analyze network traffic to identify and neutralize cyber threats.
6. Fraud detection and financial security
Financial institutions increasingly rely on AI to detect fraudulent transactions and cyber fraud in real time. AI models analyze transaction patterns to identify irregularities indicative of fraud, enabling immediate intervention and reducing financial losses.
The business case for AI-driven security
Adopting AI in cybersecurity is not just a technical upgrade; it is a strategic business decision. Organizations that integrate AI into their security frameworks benefit from a wide range of benefits including:
1. Improved threat management efficiency
AI-driven security reduces the workload on cybersecurity teams by automating routine threat detection and response tasks. This enables security personnel to focus on complex threats and strategic initiatives, improving overall efficiency.
2. Cost savings and risk reduction
Cyberattacks cost businesses billions of dollars annually in damages, regulatory fines, and reputational loss. AI’s ability to detect and prevent threats early significantly reduces financial risks. Automating security responses also minimizes the need for large security teams, optimizing operational costs.
3. Scalability and adaptability
As businesses expand their digital footprint, AI provides scalable security solutions that adapt to new technologies, cloud environments, and hybrid IT infrastructures. Unlike traditional security methods, AI security systems improve over time, learning from new data and evolving threats.
Challenges and considerations in AI security
Despite its advantages, AI-driven security is not without challenges. Organizations must consider the following:
1. Adversarial AI and AI-powered attacks
As organizations deploy AI for cybersecurity, cybercriminals are also leveraging AI to develop more sophisticated attack methods. Adversarial AI, which manipulates ML models, poses a serious risk. Security teams must continuously refine AI algorithms to defend against AI-driven threats.
2. False positives and accuracy issues
AI-driven security solutions must balance sensitivity and specificity. Overly aggressive AI models may generate false positives, causing unnecessary alerts and disruptions. Conversely, if AI is not trained properly, it may fail to detect real threats. Continuous model training and validation are essential.
3. Ethical and privacy concerns
AI security solutions require access to large amounts of data, raising concerns about user privacy and data protection. Organizations must ensure compliance with regulations such as the GDPR and CCPA while implementing AI-driven security solutions.
4. The need for human oversight
While AI can automate many security functions, human expertise remains irreplaceable. Security professionals must interpret AI-generated insights, manage complex threats, and make strategic security decisions.
Future trends in AI powered security
As AI powered cybersecurity continues to advance, the future of AI-driven security will be shaped by several key trends:
1. AI-driven Zero Trust architecture
Zero Trust security models require continuous authentication and strict access controls. AI enhances Zero Trust by analyzing user behavior in real time and adjusting access permissions dynamically based on risk assessments.
2. AI-powered cyber threat hunting
Proactive threat hunting will increasingly rely on AI to identify hidden threats within an organization’s infrastructure. AI will assist cybersecurity teams in uncovering advanced persistent threats (APTs) and nation-state cyber espionage activities.
3. AI in cloud security
As cloud adoption grows, AI will play a vital role in securing multi-cloud environments. AI-driven cloud security solutions will detect misconfigurations, monitor API traffic, and ensure compliance with industry standards.
4. Quantum computing and AI security
The rise of quantum computing poses both opportunities and challenges for AI security. Quantum-powered AI models will enhance encryption and threat detection, but they may also break existing cryptographic security. Organizations must prepare for post-quantum cryptography.
Fujitsu’s AI-enhanced security solutions
Fujitsu has been at the forefront of integrating artificial intelligence (AI) into cybersecurity, developing innovative solutions to address the evolving threat landscape.
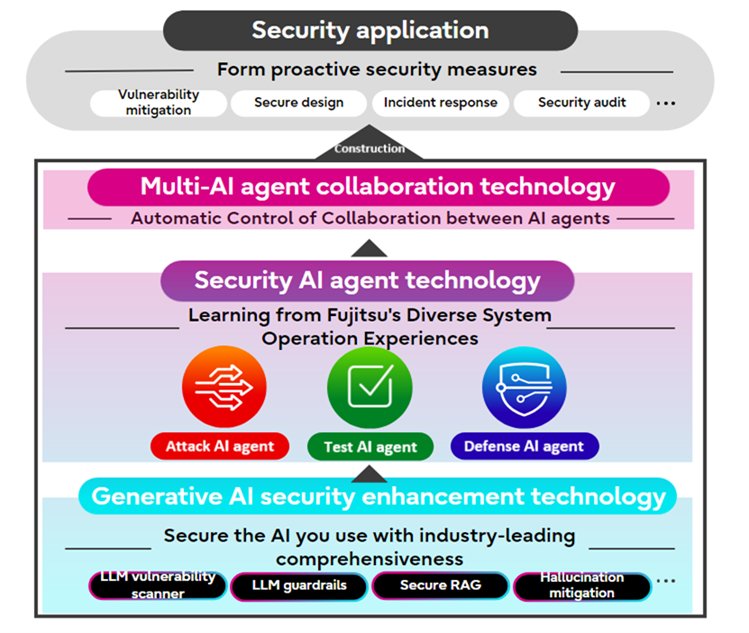
Fujitsu’s multi-AI agent security technology
In December 2024, Fujitsu announced the development of the world’s first multi-AI agent security technology. A groundbreaking suite of AI agents designed for proactive security measures, developed in collaboration with Ben-Gurion University of the Negev, a global leader in cybersecurity research. This innovative technology comprises three fundamental AI agents:
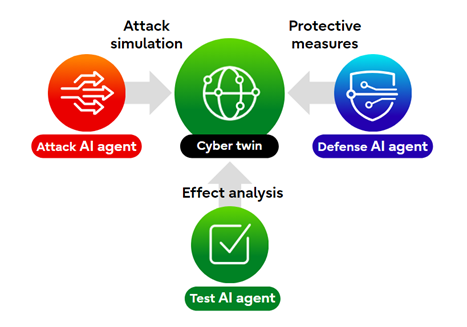
• Attack AI agent: Utilizes a Tactics, Techniques, and Procedures (TTP) analogy engine to craft effective attack scenarios against target systems, addressing emerging threats with precision.
• Defense AI agent: Tailors countermeasures based on your company's unique risk profile, ensuring customized protection against potential vulnerabilities.
• Test AI agent: Automatically constructs a verification virtual environment, or "cyber twin," from your production system. This agent conducts reciprocal attack and defense simulations alongside the Attack and Defense AI agents, enabling thorough analysis and proactive defenses against new vulnerabilities.
Our AI agents are distinguished by their co-creative learning capabilities, which address complex and unknown challenges through collaborative and adversarial learning. By leveraging diverse skills, these agents work together to tackle security issues with unparalleled effectiveness.
Multi-AI agent collaboration
This technology enables seamless collaboration between AI agents and is versatile and applicable beyond security. When AI agents collaborate, ensuring data confidentiality, privacy protection and adherence to the policies of each organization is a significant challenge. To address this, Fujitsu implemented a secure agent gateway coordination function within each organization's AI agent infrastructure. This allows for autonomous control of collaboration policies, enabling seamless AI agent collaboration without the need for explicit consideration from AI agent developers.
Generative AI security enhancement
Developed in collaboration with Ben-Gurion University, our innovative security solution offers robust protection for generative AI systems. It features two key components:
1. LLM vulnerability scanner: This powerful tool automatically and comprehensively evaluates the security resilience of your AI models. It addresses over 3,500 known vulnerabilities, including proprietary generative code issues. With adaptive prompting technology, it selects optimal attack prompts based on the model's responses, ensuring precise and accurate assessments. Additionally, AI-driven explanations make vulnerability assessments accessible to non-security experts.
2. LLM guardrails: Working seamlessly with the vulnerability scanner, these guardrails automatically detect and block malicious prompts during IT operations. By applying intelligent guard rules, they prevent inappropriate responses and ensure the safe and secure functioning of generative AI systems.
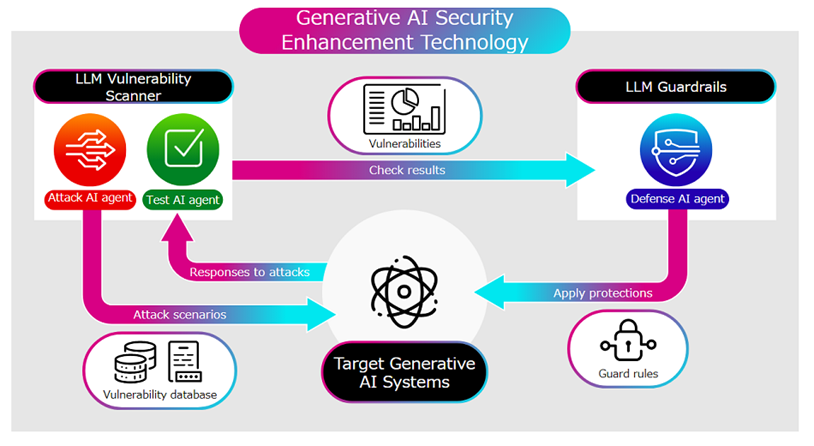
Together, the LLM vulnerability scanner and guardrails collaborate with AI-powered attack and defense agents to implement proactive security measures, safeguarding your systems against potential threats.
AI-driven data and security technologies
Fujitsu is strengthening the security of networks and AI systems underpinning social infrastructure. By developing trust technologies that ensure secure access across physical and digital spaces, Fujitsu enhances the overall security posture of organizations.
For instance, their ConnectionChain technology connects multiple blockchains, allowing for end-to-end traceability across connected ecosystems, which is crucial for maintaining data integrity and security.
See: https://www.fujitsu.com/global/about/resources/news/press-releases/2024/1212-01.html
Fujitsu intelligence-led cybersecurity services
Fujitsu offers a full range of intelligence-led cybersecurity services designed to protect business continuity around the clock. These services utilize the latest cyber intelligence to mitigate threats, safeguard data, and ensure continuous operations. Key components include:
• Cyber security consulting services: Providing independent security advice tailored to specific industry needs, including security advisory assessments, strategy development, incident management, and resilience planning. See: https://www.fujitsu.com/global/services/security/offerings/consulting/it-security/
• Managed security services: Offering comprehensive security solutions that align with regulations such as ISO22301:2012, ISO 27001/2, PCI DSS, and SOX. These services are designed to provide better protection at lower costs, with flexibility and a modular approach. See: https://www.fujitsu.com/global/services/security/
• Security operations centers (SOCs): Fujitsu’s SOC teams monitor the latest threats, respond to new security standards, and devise effective strategies to address emerging issues, ensuring 24/7 business continuity. See: https://www.fujitsu.com/global/services/security/offerings/soc/index.html
Through these and other security solutions, Fujitsu demonstrates its commitment to providing robust cybersecurity measures, enabling organizations to navigate the digital landscape securely and efficiently.
Conclusion
AI is transforming cybersecurity by providing faster, smarter, and more adaptive defense mechanisms. Organizations that integrate AI-driven security solutions gain a significant advantage in managing cyber risks, protecting critical data, and ensuring business continuity. However, AI security must be implemented thoughtfully, addressing challenges such as adversarial AI, privacy concerns, and human oversight.
As cyber threats continue to evolve, AI will be indispensable in delivering the next generation of IT security. Businesses that proactively embrace AI-driven security will be better positioned to defend against the increasingly sophisticated cyber threats of the future.
Why not talk to Fujitsu and find out how we can help you harness the power of AI to enhance your Cybersecurity?

Related information
- The future of cybersecurity - An introduction to ambient authentication
- Next generation AI trust: Powered by RAG and Graph AI
- The Rise of Shadow AI - Implications for Privacy, Security, and Ethics
- Agentic AI: The technology catalyst for the next generation of Digital Transformation (DX2.0)
- Fujitsu Enterprise Cyber Security Solutions
Editor's Picks










