
With the introduction of the Australian Government Secure Cloud Strategy, all government agencies are now pursuing a secure cloud strategy as the security posture of their cloud adoption has become of paramount importance.
A secure cloud strategy should not be left only to government agencies but instead should also be adopted by organisations that manage critical infrastructure. As a result, cloud security considerations have become an integral part of the protection of sensitive data when stored and managed within a third party cloud provider for most organisations.
Cloud security considerations are a critical component of data protection. Even if the cloud platform itself is secure, this does not mean that security will transcend to the data or applications hosted on top the cloud platform. Thorough audits, as well as practices and procedures, will need to be adhered to in order to ensure threats and risks are mitigated.
How does Cloud Security Work?
Cloud security is the relationship and interaction of technologies, controls, processes, and policies. Each of these elements must be designed with a secure by default approach, to ensure that you minimise the attack vectors and consequently your operational security risk.
There are a number of published documents which provide prescriptive guidance for each of these. If you align with the Australian Government Information Security Manual (ISM) and the Protective Security Policy Framework (PSPF), then you will be able to accelerate your security positioning.
Embedding ISM aligned cyber security practices is increasingly becoming a common practice amongst Federal and State agencies, as well as organisations responsible for maintaining critical infrastructure. Cyber-attacks by state backed actors or other individuals and organisations are a continual threat to the Australian economy, subsequently increasing the importance of our cyber security practice.
How should an agency or organisation secure their data within a cloud tenancy?
The Australian Cyber Security Centre (ACSC) has put together a white paper on Cloud Security for Tenants, designed to assist an organisation’s cyber security team, cloud architects and business representatives to jointly perform a risk assessment and use cloud services securely.
The security controls and procedures captured within the ISM are extensive and extremely detailed and therefore too deep to cover within this single article. Instead, a summary of key guidance areas have been highlighted in the diagram below and should prove valuable to your pursuit of secure cloud services.
The diagram highlights the 12 security strategies to consider when setting out on reviewing or establishing your cloud security strategy. The personality of your business will need to be considered when approaching this, for instance:
- What is your appetite for risk?
- What data classifications are you working with?
- Which individuals are accessing your systems
- Which locations are allowed to access your data?
Each organisation will have a slightly different perspective. Thus your secure cloud strategy will be built upon standard foundations, but will also have unique attributes, tailored to your specific needs.
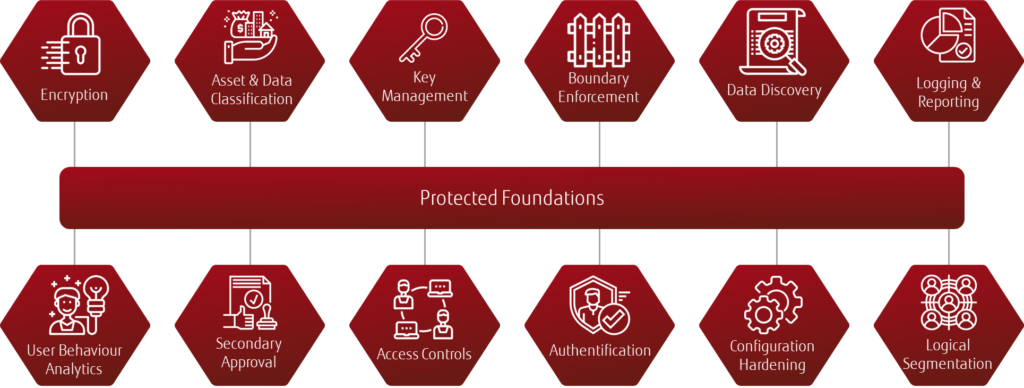
Building your secure cloud strategy
Consider the following factors when you set out to build your secure cloud strategy.
Security Risk Management
You should develop a Security Risk Management Plan (SRMP) to identify and assess security risks associated with all sensitive elements of the cloud service, while recommending suitable treatments and remediation to reduce the overall risk of the cloud service. In order for the cloud service to be implemented with minimal risk and to protect sensitive information, these systems should be compliant with Australian Governments Information Security Manual.
Account Management
Privileged accounts present a serious risk. Cyber criminals are more interested in stealing your credentials for privileged accounts than any other type of account. Thus, they present a challenge for your IT department.
You should have a Privileged and Account Management (PAM) system to control administrative access to information. Your cloud provider will either integrate directly with your PAM or offer their own managed system. A good PAM combines multi-factor authentication and user access policies, helping you control who has access to your applications and data, what they can access, and what they can do to your data.
Configuration hardening
It is good security practice to securely configure, harden and maintain your deployable operation templates to ensure that they are continually updated and making your baseline deployment secure from the get go. The Australian Cyber Security Centre (ACSC) has produced guidance to assist in securely configuring various operating systems.
Some of the hardening techniques are, but not limited to:
- preventing standard users from running script execution engines,
- disabling local user accounts,
- restricting the ability to install unapproved software
- restricting the execution of executables, software libraries, scripts and installers to an approved set.
Further detail can be found on ACSC website under Operating System Hardening.
Threat Intelligence, Monitoring, and Prevention
You need to ensure your cloud providers Secure Internet Gateway (SIG) covers the detection and prevention of potential threats to your systems should you utilise their services for internet access for your secure cloud services.
Prevention is not the only action you should take against cyber-attacks. Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS) are also a key solution to maintaining good cloud security. Threat Intelligence and IDS tools provide a way to identify cyber-attacks that are currently taking place against your systems. Intrusion Prevention Systems tools provide functionality to mitigate against an attack and alert you to the security event in a timely manner allowing you to respond quickly.
Cyber Security Incident Response Plan
If you have sensitive data within publically accessible cloud platforms, it is highly advisable to incorporate a Cyber Security Incident Response Plan into your operations in order to facilitate speedy and efficient recovery from security incidents and to facilitate a systematic response to correctly handle and contain the incident. It is important to recognise that each person has discrete roles and responsibilities for security incident detection and a response perspective. The Cyber Security Incident Response Plan should aim to identify and delineate these responsibilities.
Encrypt data in flight and at rest
While connecting to and consuming cloud services, the data you are transmitting to and from the cloud service is at risk of interception from unauthorised sources. Encryption is a key mitigation strategy used in cloud security to protect your data assets, by encoding them when at rest and in transit. This ensures the data is near impossible to decipher without a decryption key that only you have access to.
Key Management
The management of your encryption keys should be covered within your Key Management Plan. The plan should address the use and management of cryptographic keys and associated hardware and software. It includes their generation, registration, distribution, installation, usage, protection, storage, access, recovery and destruction
Cloud Vulnerability and Penetration Testing
Another practice to maintain and improve cloud security is vulnerability and penetration testing. By bringing in a Pen Tester on a consultative engagement, this will involve you and your cloud provider working with the Pen Tester in attacking your own cloud infrastructure to identify any potential weaknesses or exploits. Your Pen tester should provide you with a security report of their findings that you can then utilise in identifying and implementing solutions to patch these vulnerabilities and improve your security stance.
Logical Segmentation
Logical segmentation is increasingly common in implementing cloud security. It is the practice of dividing your cloud deployment into distinct security segments, right down to the individual workload level.
By isolating workloads into multi-tiered modern cloud architectures, you can easily apply security policies to reduce the depth within a system an attacker could reach, should they gain access, potentially only ever accessing internet facing services while the application and data set remain obscured and inaccessible.
To summarise…
Remember, the ISM and PSPF is a set of guide lines and security controls to mitigate against cyber threats. These controls are not exclusive to Federal and State Government agencies and should be applied by all organisations in some matter to form the protected foundation of their enterprise or departmental security posture.
If you have made it this far and the article has raised your awareness to securing sensitive cloud workloads, get in touch with the Fujitsu team to discuss how we can assist in improving your cloud security posture and increasing your transformational velocity for new innovations and solutions.












