Exploring protected foundations: the key enabler for an adaptive and successful future
Fujitsu / July 15, 2022
You will have probably heard the famous parable (particularly if from the Christian faith) about the 'wise man and the foolish man'. The former built his house on sand, and as a result it wasn't around for long when the storm came. The latter built his house on rock, and it stood firm in the same challenging circumstances.
It’s a religious ‘story’, but its analogy highlights the importance of making well thought-through, long-term decisions – particularly those that related to choosing/creating the right landscape on which you build and grow for the future – particularly when those times are likely to demand resilience and adaptability. The same thinking in a business context, is at the heart of a concept I call ‘Protected Foundations’.
In this blog, I’ll explore why protected foundations are needed to enable a bright and (just as importantly) safe future for your organization. I’ll dig into what your key priorities should be when producing these and share some practical views on the initiatives you’ll need to master for success.
Contents
- Being strong and sustainable for ‘transformed transformation’
- You need to Connect, Protect and Regulate
- Initiative one - Connect a dispersed organizational landscape
- Initiative two - Protect data, digital assets, and critical services
- Initiative three – Regulate for complete confidence in your compliance
- Helping you to create and continuously optimize your protected foundations
Being strong and sustainable for ‘transformed transformation’
Digital transformation is well underway amongst organizations across the globe. In fact, Foundry research tells us that when it comes to adopting a digital-first business strategy, an enormous 91% of organizations either already have their approach in place, or have plans to adopt one. (*1)
It’s no surprise. The huge technological advances and societal and environmental change that has touched every one of us means nothing can stand still – not even transformation strategies themselves. Our own research revealed that 64% of organizations are scrapping or re-thinking their long-term transformation strategies which were usually multi-year programmes that promised ‘big-bang’ results – and often replacing them with something more iterative that provides continuous, incremental value.
This new approach shifts the velocity of transformation up a gear. And the IT and OT (operational technology) that underpins it swells, in terms of both volume and variety. So, the foundations you create need to be strong and robust enough for today’s requirements, but sustainable and fit for the future as this velocity, volume and variety continues to surge. Making sure this is the case has plenty of benefits, some of which are shown here:
(*1) Foundry, 2021 Digital Business report, 2021 https://resources.foundryco.com/download/digital-business-executive-summary
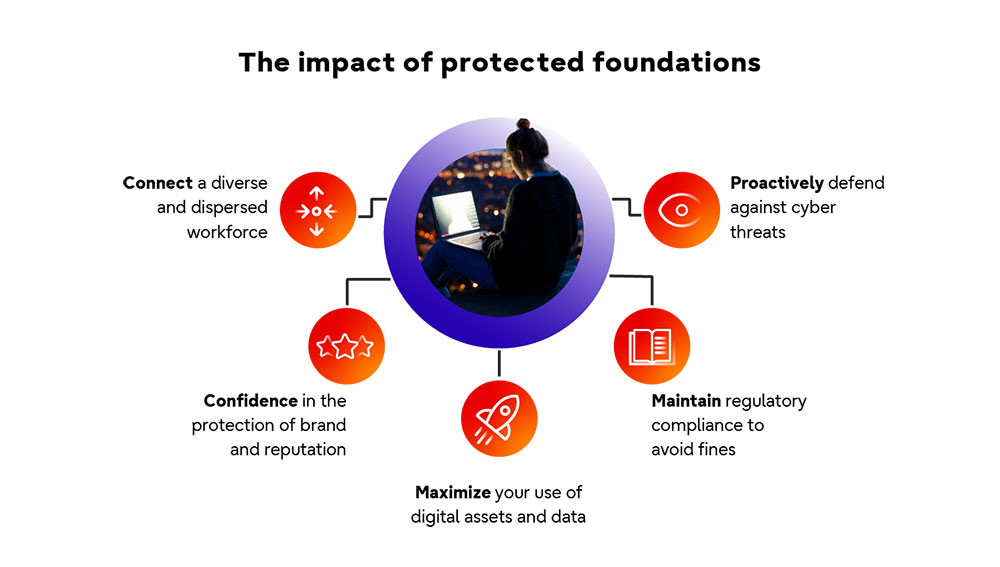
There are many advantages to protected foundations, in particular building a resilient, future-proof core to support your journey.
You need to Connect, Protect and Regulate
I couldn’t sit here and tell you that Protected Foundations are important without giving you some key areas to focus on for success. I think there are three outcomes to target. You should strive to:
1. Connect a dispersed organization landscape
2. Protect data, digital assets, and critical services
3. Regulate for complete confidence in your compliance
Doing this well enables organizations to safely embrace the new technology and business concepts that will address both immediate needs and long-term ambitions. Take VTT, for example, who worked with us to introduce greater collaborative working, more proactive security, and tighter compliance – outcomes now enabling their business transformation – all of which are enabled by a secure, resilient, cloud-based infrastructure.
Below, I’ll take a closer look at the areas of ‘Connect, Protect and Regulate’ in turn, while offering points of view and guidance, to help you start thinking about how to navigate these successfully.
Initiative one - Connect a dispersed organizational landscape
We understand that, as you digitally transform, your operational landscapes will become more widely distributed. Not least because your employees need to work collaboratively across larger and more diverse ecosystems - and access IT/OT systems and information from remote locations. And that’s before we even touch on the wider world… that is, how you serve customers’ evolving needs.
These will cause your landscape to disperse further. Not only will they expect to be served increasingly through digital-only or omni-channel services; but edge-based data processing will also need to proliferate – to enhance the accessibility, responsiveness, and quality of these, so you can remain competitive and/or valuable.
The operations and services in question – and the now sprawling infrastructure, applications and data that needs to serve all these needs to be connected. So, what do you need to focus on?
The first thing in my mind is giving employees timely, flexible, and secure data access. With operational pace now a key trait to strive for, many organizations are shifting towards a more autonomous culture – a decentralized approach – to facilitate rapid response. Employees are trusted with an increasing amount of decision-making based on data insights. This means that data becomes democratized – and so two things that you should look to embed are an internet-first approach to connectivity (typically underpinned by a cloud or hybrid IT architecture) and the enforcement of a central but adaptable set of connectivity policies, enabled by a modern SD-WAN.

The changes organizations need to make will require new technology and processes, but also a new cultural approach.
Particularly with the reach of hybrid environments now extending (beyond the data center core and cloud) to the edge, an internet-first approach and adoption of SD-WAN often needs to be supplemented by a secure cloud gateway to control network traffic from a central point, particularly if looking to move data across your environment using your own private networks. You may also wish to invest more heavily in endpoint encryption, so that data is 'shielded' as it moves through the cloud to the broader environment in either direction.
There are of course other connectivity considerations – but the biggest one of all is to ensure you understand the latest relationships and dependencies across your entire IT/OT environment through regular and continuous assessments. This naturally evolves in every organization and increases the capacity for a negative ‘domino effect’ – if any alterations are made without the very latest view – and there have been some high-profile examples where even the smallest oversight has caused an interruption to an organizations’ live service. So, my message is ‘assess as you continue to adapt’.
Initiative two - Protect data, digital assets, and critical services
Obviously, one of the worst-case scenarios for any organization is a security breach – and the cost of a breach is not only felt in the loss of business-critical data. Firstly, in a more tightly regulated world, the scale of fines can cause a financial disaster for many organizations. And secondly, in the digital-first era of customers being able to move quickly and easily between providers, the amount of reputational damage – and the loss of consumer trust that a breach can cause – is enough to threaten the entire existence of many businesses.
There are plenty of things to cover, to avoid the nightmare scenarios unfolding. But I think there are two major areas to direct your focus, to remain protected at all times.
The first is the increased attack surface caused by the increasingly distributed nature of your organization, as we touched on from a connectivity standpoint earlier, coupled with growing multi-cloud adoption and an ever more complex ecosystem of partners involved in delivering services. Your overall security posture needs to change as quickly as this happening.
Theory, you can break this down this down into the classic ‘people, processes and technology’ buckets – but in reality, these need to be collectively addressed as a joined-up whole.
- People – employees are often the weakest link in your security armour. From unwittingly opening the door to malware through email attachments to falling foul of false identities, your staff are responsible for up to 90% of data breaches.
- Processes – In recognition that every organization will inevitably fall victim to a cyber incident at some time, your cyber security processes need to be evolved, improved, and, critically, practiced. security of processes and processes for security.
- Technology – an increased number of platforms, applications, data and devices which extend beyond traditional security boundaries, as the end-point is the new permitter.
The second area to focus on is the evolving sophistication of cyber-criminal tactics and malware. To combat these advancements, your specific security solutions and approaches need to become more proactive and intelligent than ever before. Something I advocate is building/gaining capability in ‘Managed Detection and Response’ rather than (or as well as) perimeter-based security measures.
In my opinion, when building this capability, it should be based on the key principles of being 360-degree in scope (holistic, always-on, real-time analysis), being heavily automated (able to identify, link, prioritise and tackle a high volume of incidents), and able to continuously learn from previous incidents and self-improve with the help of AI. We’re helping many customers to act on such principles to shut down emerging security threats, just like with UK energy provider Scottish Water.
Initiative three – Regulate for complete confidence in your compliance
As if keeping up with the pace of change and the ever-widening threat of a cyber-attack wasn’t enough, regulation is also forever-evolving and – for most organizations – becoming more stringent. Gartner research predicts that by 2023, 75% of the world's population will be covered by modern privacy laws, and that by 2024, 80% of global companies will face more modern data privacy and protection requirements.
Modern compliance strategies need an integrated ‘three-pronged’ approach. First, one that tackles cross-industry fundamentals as new legislation is introduced and existing legislation is updated. Typically, this is slower to move and therefore more visible further in advance – like GDPR being introduced in Europe a few years ago, for example.
Second, a prong that addresses geographical or industry-specific regulation, which is nowadays the fastest moving and more likely to be tweaked and changed over time, as industry-regulators strive to enhance the protection of personal data, consumer privacy rights, and societal trust.
The third strategic ‘prong’ is fast-emerging as something far beyond a regulatory compliance need; it is becoming central to every organization’s strategic direction and future business model. That is, delivering on sustainability commitments – which for many companies exist in the form of Environmental, Social and Governance (ESG) targets.
So, with three lots of regulatory requirements to deliver on – does compliance have to mean compromising on agility and growth? My view is that with the right foundational technologies underpinning your transformation strategy, regulation can and should be treated as an opportunity, not a threat. In other words, while simultaneously keeping up with changing regulatory needs and customer requirements will always have some degree of balance, it doesn’t need to be a trade-off as they are intrinsically linked. GDPR for example, gave organizations the opportunity to optimize their data strategy, cleanse their records and be more relevant and trusted in the eyes of their customers.
ESG targets are encouraging organizations to build their future business model, so they can compete responsibly and sustain success in the right way for our planet and society for years to come.
And, thanks to the rapid evolution of (and huge investment in) secure, highly-regulated cloud services, organizations are now finding that the technologies they need to act on this shift in mindset can be embraced to transform their IT and OT environments with confidence, rather than having to tread overly-cautiously around them. More specifically, with multi-cloud or hybrid cloud models on the rise still, organizations are finding themselves much better placed to satisfy what would have, in the past, been many conflicting needs across all three regulatory prongs I’ve mentioned.
Helping you to create and continuously optimize your protected foundations
Your foundations aren’t just something to be deployed in a single project – they need to be continuously improved and optimized to ensure your business has the best connected, protected and regulated environment to deliver digital transformation in a strong and sustainable way.
Fujitsu has the trusted experience and on-demand expertise to help you create and continuously enhance your Protected Foundations. From financial services and government to retail and manufacturing we have done it for organizations with some of the most challenging connectivity, security and regulatory requirements… and we can do it for you, too.

Currently, Stuart leads the Networks and Security Value Stream for Fujitsu North Western Europe focused on developing products and services that address customer business challenges.
Related information
Editor's Picks











