Secure your SilverStripe site: Your guide to fixing CVE-2024-47605 cross-site scripting vulnerability
Fujitsu / June 17, 2025
The constant threat of website security
Website security is a constant battle, and content management systems (CMS) are often a prime target to cyber-attacks.
While performing a website penetration test for a client that was using the SilverStripe CMS, Fujitsu Cyber discovered a security flaw that allowed attackers to inject dangerous JavaScript code simply by embedding content from a malicious website.
This vulnerability, now patched and registered as CVE-2024-47605, had the potential to compromise both editors and site visitors.
This post explains our discovery, the vulnerability’s mechanics, and the steps taken to mitigate the threat.
Proof of Concept
Unveiling the vulnerability: How malicious code bypassed security
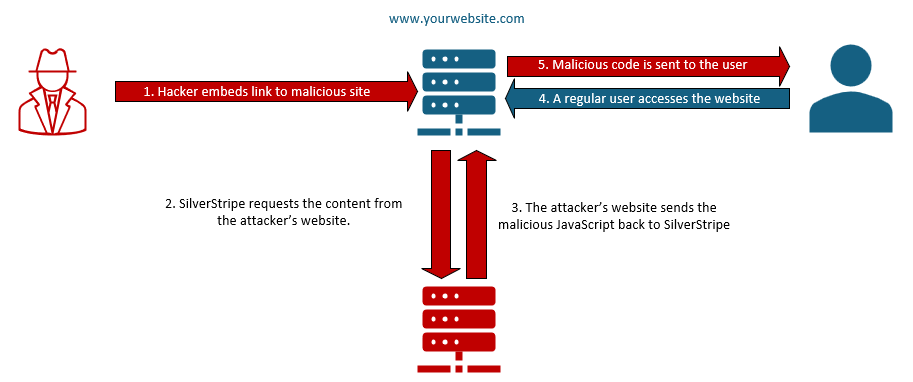
SilverStripe CMS lets users add content from external sources by pasting in a link, or URL, of third-party content.
This uses a feature called “oEmbed”, which is a commonly used format to instruct other websites on how to display the inserted content. This allows people to embed videos, images, and other content from third-party websites into their webpages.
The problem was that SilverStripe wasn't properly checking content from third-party sites. A malicious link disguised as a valid media source could inject harmful code directly onto the webpage, bypassing any security filters.
That’s a textbook example of a security issue called Cross-Site Scripting (XSS).
Attack Diagram
Exposing the flaw: Our step-by-step discovery process
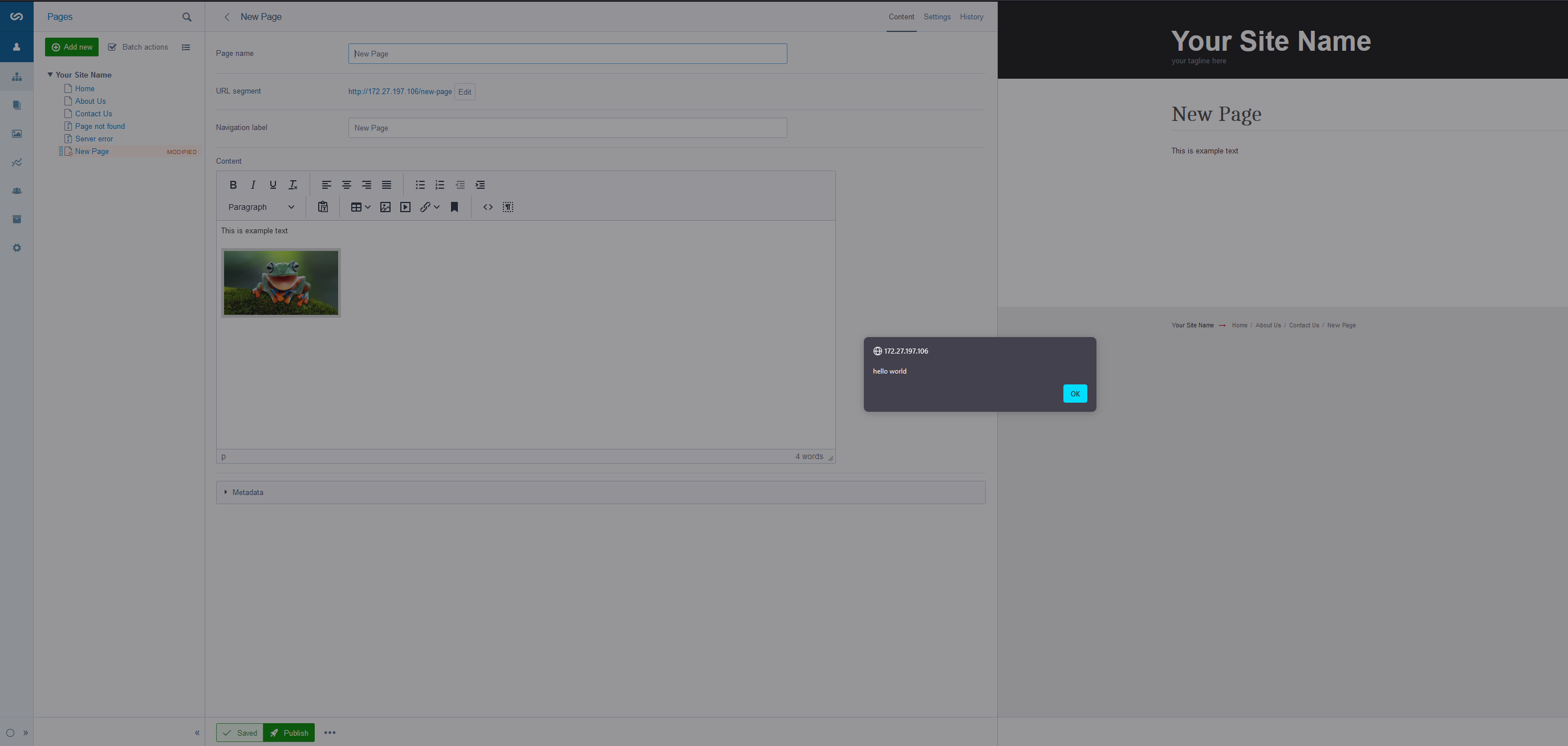
To demonstrate the vulnerability, we set up a basic server that responded with a fake oEmbed response.
Instead of valid media content, it returned a small piece of JavaScript code that would show a popup saying, “hello world.”
Walkthrough:
- 1. Set up a SilverStripe CMS site (version 5.2).
- 2. Logged in as a user with editing permissions.
- 3. Clicked “Insert Media via URL” in the page editor.
- 4. Pasted in a link to our test “hacker” server, which returned the malicious data.
- 5. Saved the page.
At that point, the script we injected would run every time someone viewed the page in both the editing area, and the public website.
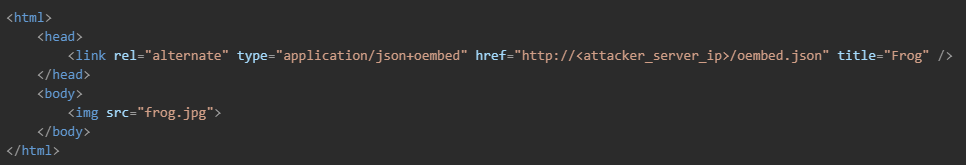
Our test “hacker” server hosted a page with the following HTML code, linking to the malicious oEmbed JSON file:
Malicious Website code
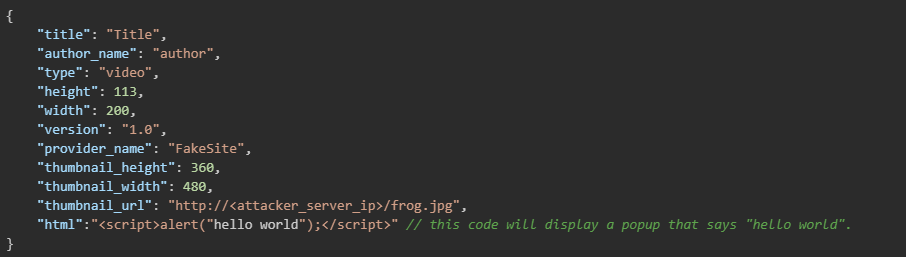
The malicious oEmbed JSON file contained the following information:
Malicious JSON
Then, we inserted the content into our SilverStripe test server:
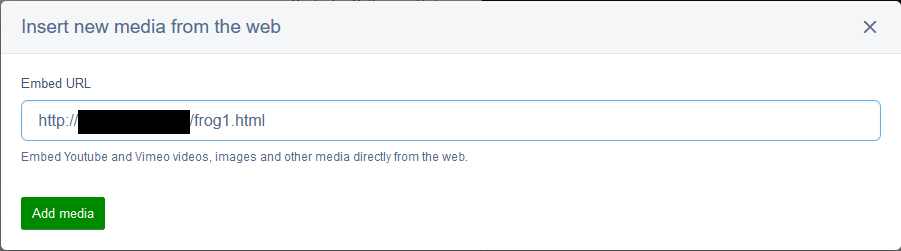
Insert Media Prompt
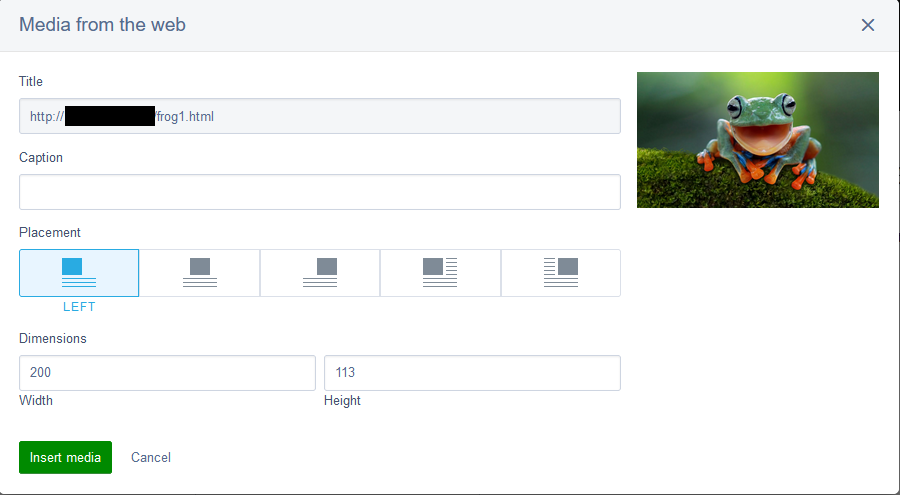
Media from the web Prompt
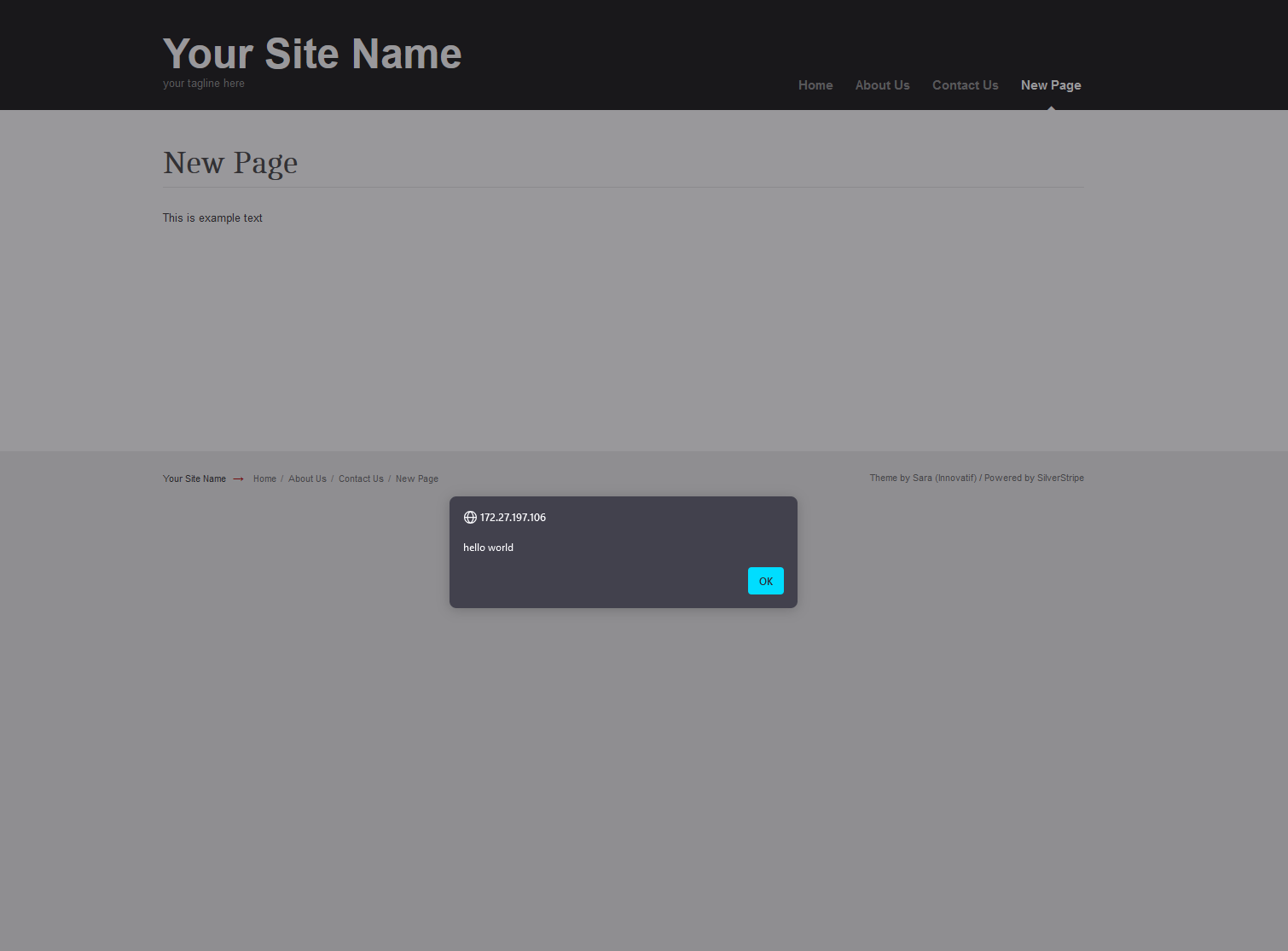
The results
The impact: Why this vulnerability matters
This flaw meant an attacker could trick an editor into embedding a malicious link and unknowingly introduce a security hole into the website.
Because the injected code ran in the browser of anyone viewing the page, attackers could have used it to:
- Steal user login credentials.
- Deface website content.
- Redirect users to malicious websites.
Protecting your site now: immediate actions
SilverStripe responded quickly and patched the issue in version 5.3.8. If you’re running an older version, you should update immediately.
Even if you’re not using oEmbed features often, vulnerabilities like this one are reminders that all third-party content should be treated carefully. If your site accepts input from others, it needs to validate and sanitise everything it receives.
Key takeaways and best practices
We’re always glad when responsible disclosure leads to quick fixes and safer software. If you’re a developer, editor, or administrator using any CMS, this is a good time to review how embedded content is handled on your platform.
Stay safe, and patch often.

