Moving to the cloud brings enterprises significant cost benefits and puts the latest development technologies, tools and applications at their fingertips. These advantages have led to the widespread adoption of cloud computing as the foundation of businesses’ digital transformation.
And the growth we’ve seen to date will only accelerate.
According to a recent Gartner survey of public cloud users, 81% said they are already working with two or more providers, while more than a third of organisations now consider cloud investments as a top three investment priority.
Based on the growing maturity of the cloud market and the corresponding experience that organisations are accumulating, they are also becoming more discerning in terms of how they use cloud services. Increasingly, deployment is more closely aligned to specific business outcomes, with the choice of cloud platforms to help achieve objectives.
As a result, businesses increasingly deploy multiple public clouds, each optimised to handle different functions.
Cloud adoption extends the corporate threat landscape
The benefits of cloud adoption are undeniable – including lower costs, faster rollout of new services and accelerated time to execution. But on the other hand, cloud also brings additional security considerations, since data is moved outside the control of traditional on premise data centres.
This extends the corporate threat landscape; and ultimately increases the cyber-attack surface available to criminals, increasing the likelihood of data loss, and opens businesses up to new dangers, not only revenue and productivity but also the potential loss of brand equity – their corporate reputation.
To mitigate these additional security considerations, businesses must understand where the responsibilities lie for protecting the cloud infrastructure and the data that lives on it.
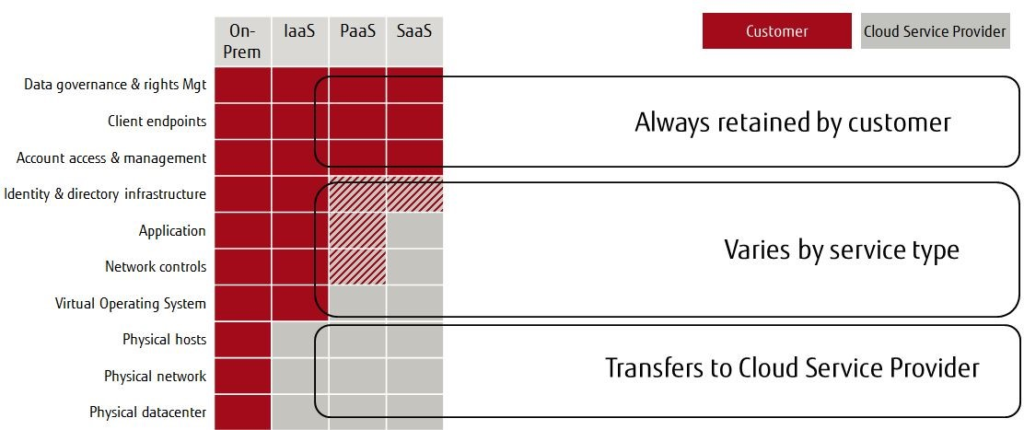
A consensus has formed on the so-called waterline that delineates this shared responsibility: above the line is down to individual businesses while managing anything that falls below the line is the responsibility of the infrastructure provider. This waterline is not static, however – it moves depending on the cloud services that a business consumes.
Where do you draw the demarcation line for responsibility?
For example, for an organisation running everything on-premises, then the customer has responsibility and control of everything, from the data centre itself to networking, storage, and security.
But when elements are moved to the public cloud, that responsibility changes. Although cloud service providers are always responsible for the security of the cloud platform itself, the customer is still responsible for the security of the data it places in that cloud.
Accountability for other areas, including network controls, operating system, application controls, and identity management still varies depending on the cloud service model.
As customers move from Infrastructure-as-a-Service (IaaS) to Platform-as-a-Service (PaaS) and then to Software-as-a-Service (SaaS), they are responsible for less and less, while cloud service providers take on more.
The bottom line is that businesses must be clear about which elements they are responsible for, in order to secure them effectively. That’s when the native security embedded in leading clouds including Microsoft Azure, Amazon Web Services, Google, Oracle and VMware looks like an attractive proposition.
But with multi-cloud environments, it can get complex very quickly – and can lead to the inconsistent application of security policies and controls, as well as a corresponding lack of visibility across entire environments. Deploying native security features can also make transitioning workloads between clouds complex.
For example, if a customer wants to move a specific workload to a more cost-effective or better-performing public cloud, they must be able to seamlessly transition all data and security controls. In particular, sensitive data protected by standard encryption by cloud provider A must be decrypted, moved, then encrypted again using cloud provider B’s tools.
A more strategic approach comes from cloud-agnostic controls
Fujitsu provides a strategic approach, with cloud-agnostic controls that can be applied across an entire multi-cloud environment.
This provides a secure journey into cloud adoption with a complete portfolio of cloud-agnostic tooling that delivers identity and access management, infrastructure protection, threat management and data protection. By abstracting security from the actual clouds themselves, businesses can ensure better visibility over their data and applications, enjoy standardised, centralised controls, plus increased flexibility and seamless data portability.
This in turn helps to mitigate the risk of vendor lock-in and reduces the complexity and cost associated with migrating between cloud service providers.
Securing hybrid IT environments spread across multiple clouds is complex and challenging. Get in touch with our cloud experts to see how we can help your organisation get it right.