Never trust, always verify: Zero Trust
Fujitsu / September 5, 2024
In a rapidly advancing technological landscape, cyber security has had to constantly evolve to be one step ahead of the latest risks and threats. If malicious actors gain access, they can disrupt vulnerable systems, steal sensitive information, steal identities whilst pretending to be legitimate users and infiltrate connected networks.
With online financial information and data being the equivalent of mobile digital oil, hackers are driven to find vulnerabilities and leverage zero days to exploit legacy services, consumer devices, operating systems and applications. Traditional security strategies based on a secure perimeter are ineffective against the modern interconnected digital ecosystem and its expanding threats. This is where the Zero Trust model comes into play. At its core, Zero Trust operates on a principle of ‘never trust, always verify’, shifting cyber from a perimeter-based approach to an comprehensive, continuous verification process.
Core principles of Zero Trust security
Where systems rely on inherent trust within a network i.e. trusted devices, Zero Trust assumes that threats exist both inside and outside a network, guilty until proven innocent. With traffic continually queried both outside and within a network, Zero Trust relies on three principles:
1.Verify explicitly: Strict verification for every access request or interaction, such as Multi-Factor Authentication (MFA), biometric verification, certificate validation, and continuous monitoring of assertion and conditions to validate that users are who they claim.
2. Least privilege access: Users, systems and devices are granted the minimum level of access necessary to perform their roles. This includes just in time access elevation – only holding privileged access for the period of use. This reduces the potential blast radius compromised accounts / devices can inflict on an environment, while also increasing the likelihood of detection of malicious activity.
3. Assume breach: Organizations should operate as if a breach has already occurred or is imminent, ensuring robust detection and response mechanisms are deployed, and malicious activity can be quickly identified and neutralized.
Government initiatives and international standards
To enhance security for both consumers and organizations, Zero Trust has gained support from government, cyber security authorities and vendors alike. For example, in Australia, government, through the Australian Signals Directorate (ASD) Information Security Manual (ISM) encourages implementing Zero Trust through Zero Trust Architecture (ZTA). This architecture is purposefully built to reduce attack surface, prevent lateral movement and, minimize the risk of a data breach based on the Zero Trust model.
Internationally, cyber security authorities such as the National Institute of Standards and Technology (NIST) are working with the industry to define the foundational principles of ZTA. They are working to develop and standardize technologies and practices necessary to implement ZTA in critical and emerging network technologies, including incorporating ZTA into emerging standards for 5G and 6G wireless standards.
Complementing the NIST work, the United States transition to a Zero Trust future was cemented when the Biden administration announced a directive, Executive Order 14028 for the US government to attain ZTA by 2024. This directive requires US agencies to identify a Zero Trust strategy and implementation roadmap. To facilitate this transition, the Cybersecurity and Infrastructure Security Agency (CISA) has developed a Zero Trust Maturity Model. This model comprised five pillars - Identity, Device, Network, Application and Workload, and Data – and outlines how CISA can support organizations in achieving their Zero Trust capabilities.
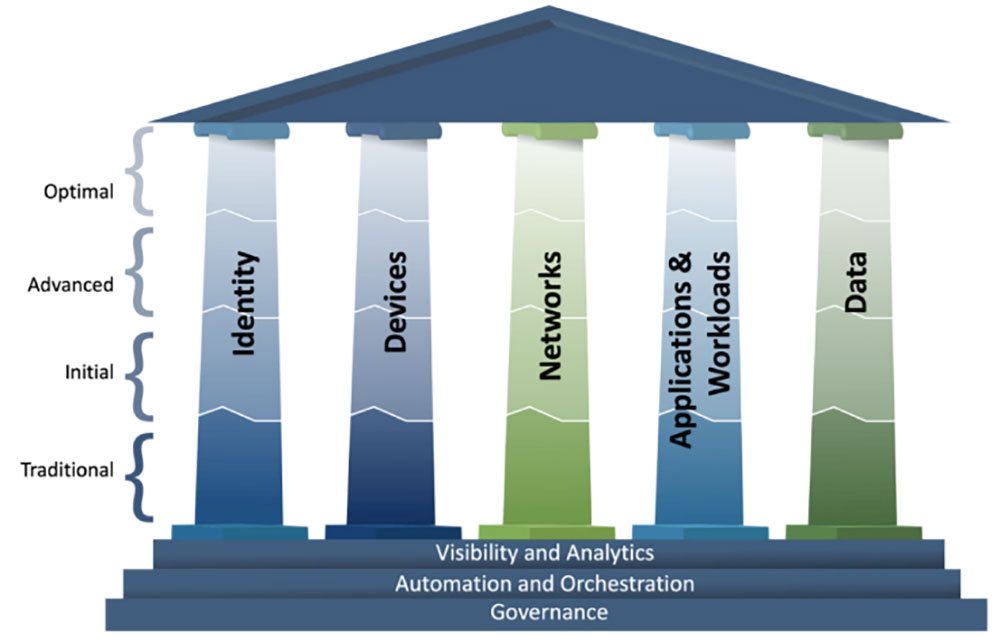
Source: CISA
Each pillar represents a critical component of a holistic Zero Trust strategy.
• The Identity pillar ensures that users are authenticated and authorized.
• The Device pillar focuses on securing endpoints.
• The Network pillar addresses secure access and communication.
• The Application and Workload pillar ensures that applications are secured and operate as intended.
• Lastly, the Data pillar emphasizes protecting data at rest and in transit.
CISA's model also outlines pathways and best practices to guide agencies through the maturity levels of Zero Trust implementation, from initial assessment to full deployment.
Conclusion
With the goal of embedding security by default, making access control enforcement the new network boundary and assuming breach when monitoring your environment, Zero Trust has redefined how consumers and organizations can safeguard their digital assets, keep malicious actors at bay, and maintain the trust of their stakeholders.
Embracing Zero Trust is not just a technological upgrade, it’s a fundamental change in how security is perceived and implemented. Fujitsu hopes to partner with you on this journey - paving the way for a more secure digital future.

Related information
Editor's Picks






