Manufacturers’ net-zero ambitions are only as robust as their OT data
Fujitsu / December 14, 2022
It’s Operational Technology (OT) data that describes what’s really happening during manufacturing, says Jamie Wilkie, Director for Industrial Security Offerings, Global, at Fujitsu. However, OT data is often sealed off from the wider IT environment and its analytic capabilities. That needs to change if manufacturers want to understand and reduce their carbon footprint.
Manufacturing and climate change
Do manufacturers truly have the necessary information to measure carbon emissions from their production?
It’s a vital question if humankind is to halt global heating before it is too late. Today, nearly 20% of global greenhouse gas emissions come from manufacturing industry, according to the International Energy Authority (IEA). On current trends, by 2050 the growth in global population and associated demand for manufactured goods will require at least twice the energy and materials we currently consume.
Most manufacturers now understand their responsibilities to the environment and change is underway. The need to achieve sustainability goals is exacerbated in the current energy crisis, which impacts both the availability and cost of fossil fuels. It is imperative that producers optimize their production processes to reduce energy use or to synchronize production with energy availability using, for example, ADR – Automated Demand Response. Production data provides key insights to achieve this.

Do manufacturers truly have the necessary information to measure carbon emissions from their production?
Change rests on data
Although there is only an extremely narrow window to slow and halt global heating, the ability to measure accurately full-lifecycle CO2 emissions is still a work in progress. Often emission figures are just aggregated estimates for a process, workshop, or factory — not detailed analyses based on hard data, machine by machine. And if you can’t measure your CO2 emissions, how can you know if you are meeting your company’s Environmental, Social and Governance (ESG) commitments?
Without solid data, it is hard for manufacturers to know precisely where to target improvements and how to obtain the maximum impact from any investment. Under these circumstances, trial and error causes delay at precisely the time when any margin for waiting has already been used up.
The root issue is that manufacturers’ ability to zero-in on investments in carbon reduction relies on data from production equipment. Generally speaking, that data is easier to obtain in areas of manufacturing operations that fall within the IT domain (Enterprise Resource Planning (ERP) systems, for example, or scanners), where data is easily captured, analyzed and managed. The physical layers of equipment (OT), on the other hand, are often hard to reach for data analytics purposes. Frequently they produce data in specialized formats that cannot easily be integrated into an IT environment for analysis.

Without solid data, it is hard for manufacturers to know precisely where to target improvements
Integrating data across different IT and OT protocols
The challenges of OT speaking to IT, and vice versa, are well known and have numerous effects. Imprecise CO2 emissions data is one of many reasons why most manufacturers are trying to deal with this.
It’s not a new issue and efforts to integrate IT and OT go back decades. In the 1990s, the Purdue Enterprise Reference Architecture (PERA) was developed by the Industry-Purdue University Consortium for Computer Integrated Manufacturing. It’s a model for enterprise control. This can be shared by end users, integrators and vendors to integrate applications across five layers, where layers zero to three are the OT equipment typically found on the shop floor and layers four and five contain business logistics systems, for instance ERP software.
One major challenge is that there are likely to be many data sources across multiple OT systems where data is not harmonized. That’s because factories typically have several different automation line suppliers, all with different protocols. The solution is to harmonize via the OPCUA (Open Platform Communications Unified Architecture), an initiative that is enabling integration of disparate data protocols. OPCUA makes it possible to see, for example, valve parameter values in China or Belgium in the same format, leading to more reliable process reporting and more meaningful CO2 emission readouts.
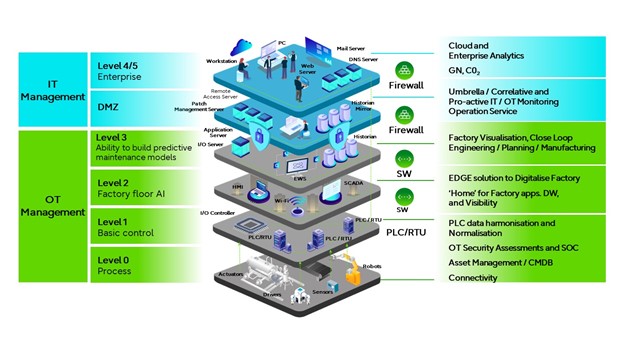
The Purdue Enterprise Reference Architecture (PERA) was developed by the Industry-Purdue University Consortium for Computer Integrated Manufacturing
Dealing with the security concerns that come with connectivity
An integrated IT/OT environment brings multiple business benefits but cybersecurity challenges too. OT has traditionally been sealed-off from IT networks and therefore less exposed to the risk of attacks such as ransomware.
However, OT is no longer air-gapped from IT in the way it once was. Cyber criminals are exploiting this change, and several high-profile cases involving manufacturing environments, such as Stuxnet and the Colonial Pipelines attack, show the risks of adding connectivity. If a bad actor gains access to your Industrial Control System (ICS) in PERA level 1-3, they have an open door to all your equipment, and production can be stopped or slowed down.
It's a dilemma because without connectivity there is no digitalization. Therefore, very few companies are deciding they have the option to keep OT isolated. As a consequence, managers must invest in OT cybersecurity to support the new paradigm as securely as possible, maintaining production uptime and ensuring physical safety.

OT is no longer air-gapped from IT in the way it once was
How to get started safely
We recommend that manufacturers go about IT/OT integration in a controlled way, building-in cyber security right from the start. Our approach at Fujitsu is to separate IT and OT in the cybersecurity context but combine them when it comes to dataflows.
The first step on that path is all about visibility. Initiate an assessment to understand your current OT security posture and how it relates to business risk. Not every risk is the same. If you are a ceramics company, then a vulnerability in a coffee machine does not have the same priority as one in a furnace.
People are often overlooked in security risk. Any assessment should cover people’s roles, responsibilities, and training. Processes are vital too. They are standard in IT but do incident response processes also exist for your OT? What if something goes wrong at 2am on a Sunday? Is there a phone call? And who gets it? Assess your technology too, to reveal the networked assets in use in OT, before starting to conduct any necessary improvements. For example, nearly all manufacturers give key equipment suppliers remote access to their networks so they can monitor when maintenance is needed. But few, in our experience, know exactly how many of their suppliers have network access.
Knowing what and where your assets are – and what state they are in – is the first step to extracting valuable data and actively managing their availability. Asset discovery, typically part of a security assessment, enables the creation of a configuration management database (CMDB).
With core visibility now in place, move on to introduce continuous visibility via a managed monitoring security service that picks up abnormal behaviors in the network, such as an unscheduled installation that might be the precursor to a cyberattack.
The reward for this work is the ability to extract data from your OT equipment and put it to work in technologies like digital twins, data lakes, and Fujitsu’s Digital Annealer – with immense potential to drive manufacturers towards net-zero targets. Secure access to accurate production data is the foundation of a successful sustainability strategy.

separate IT and OT in the cybersecurity context but combine them when it comes to dataflows

Editor's Picks







