
I had the pleasure of hosting an exec round table event this week, which was focussed on rapid innovation powered by public cloud adoption. I love these events, and not because of the excellent catering! It gives me a fantastic opportunity to reconnect with the real issues that business leaders here in Australia are grappling with on a day to day basis.
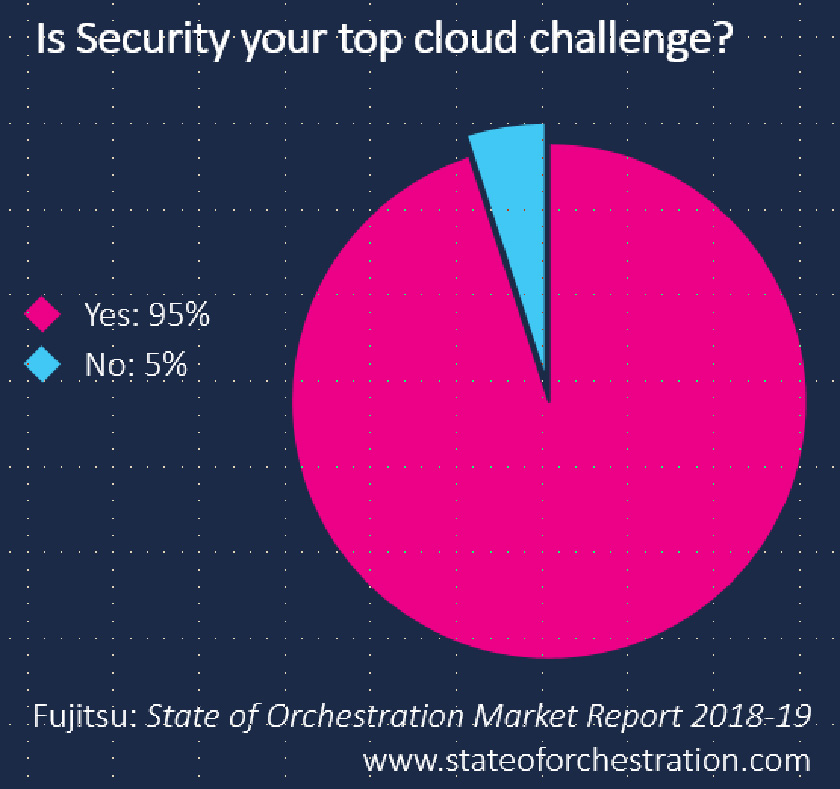
Remarkably, or perhaps not, the data and security topic is front and centre in many minds and plans, and considering that 30% of organisations both data and revenue during an attack, I can understand why. A secure by default approach to cloud design with zero trust architectures is inherent in most transformation projects, however there are still underlying concerns. In the last 2 years of research for the State of Orchestration, security has been nominated as the toughest aspect in planning a cloud first future.
It has been accepted for some time now, that traditional boundary based security for common on premise systems is weak. I’m constantly staggered by the lack of the most basic security patches in some organisations, human effort, distraction and a lack of automation are all pervasive with many traditional implementations. Adopting cloud can feel like a security anti-pattern to some, who like to know that their data is locked away in their building and they can go and physically touch it, should they feel inclined, however luckily I haven’t heard this argument for a few years!
Instead, cloud brings fantastic opportunities to increase your security and compliance posture. The inherent capabilities of Identity and access management, encryption, logging, DDos Mitigation are tightly integrated to the native cloud services and provide easy protection. That is further bolstered by policy controls such as just in time admin, geo restrictions and continuous compliance, which all add up to give you a super secure architecture.
Human error, is still one of the biggest risks, poor decisions a lack of knowledge and sometimes an over exuberance for high velocity can lead to mistakes. It is imperative that everyone understands that security is their responsibility, it is everyone’s responsibility. Luckily, even human error can be overcome by applying best practise policies from your cloud scaffolding up to your application deployments. These policies can be easily reported on and again, you can employ native functions to auto-remediate, quarantine and alert on policy breaches.
Continuous Compliance
If compliance to industry standards is your thing, do not fear hyper-scaler cloud platforms are packed full of compliance standards, can reduce your implementation and audit times by months, even years! If CSA, ISO, PCI/DSS or SOC are on your to do list, then you’ve come to the right place!
You can even get by in Federal Government, Fujitsu Protected Cloud and Microsoft Azure give support for both unclassified and protected data, with IRAP assessments and certification by the Australian Cyber Security Centre. Now this still isn’t as easy as it sounds, but Fujitsu has a lot of experience with projects and services with federal requirements and controls. If you need any advice, please reach out.
Data Sovereignty
In more recent news, the Australia and US governments are collaborating with data sharing laws as part of the CLOUD act (Clarifying Lawful Overseas Use of Data Act). In due course, this will allow both countries to make requests for electronic data to be provided by the other country. This has been on the cards for a while, but should make life easier when dealing with US based cloud service providers.
Ultimately, cloud-based security practices are making us more secure, however the threats are also escalating. There are more sophisticated, hostile actors and targeted attacks than ever, and the last thing you want is to make front-page news for a security breach, especially considering that 20% of organisations lose customers during an attack.
Here at Fujitsu, our number 1 priority is security. Absolutely everything is designed to be secure by default, with the best design patterns, methods and services to keep you safe. Our Cloud Security Assessment service has helped clients all over the world to identify vulnerabilities and remediate them. If you believe you are due a cloud security health check, please contact me directly and we’ll get you going straight away.
Find out more about Fujitsu's Secure Government Cloud Services here.












